Two-Way Document Trust
Protect what goes out with invisible fingerprinting and leak detection. Verify what comes in with tamper detection and integrity scoring. Complete document security in both directions.
Invisible Fingerprinting
Our advanced fingerprinting technology embeds unique identifiers within your documents that persist through various transformations. These forensic markers are imperceptible to the human eye but allow us to identify the exact copy and recipient of any leaked document.
- Survives screenshots and screen captures
- Resistant to compression and format conversion
- Withstands cropping and modifications
- Embedded across all pages automatically
- Imperceptible to document viewers
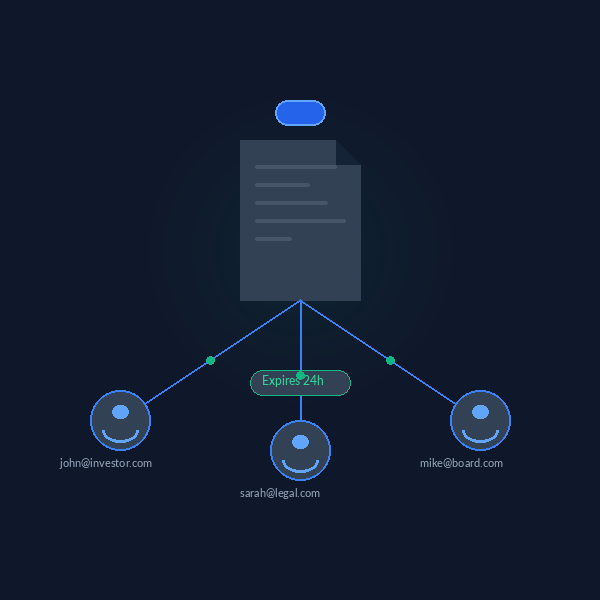
Secure Document Sharing
Share your confidential documents through unique, tracked links that you control completely. Set expiration dates, revoke access instantly, and view detailed analytics about who accessed your documents and when.
- Customizable expiration dates
- One-click access revocation
- Unique tracking links per recipient
- View count and access duration monitoring
- Device and location information logging
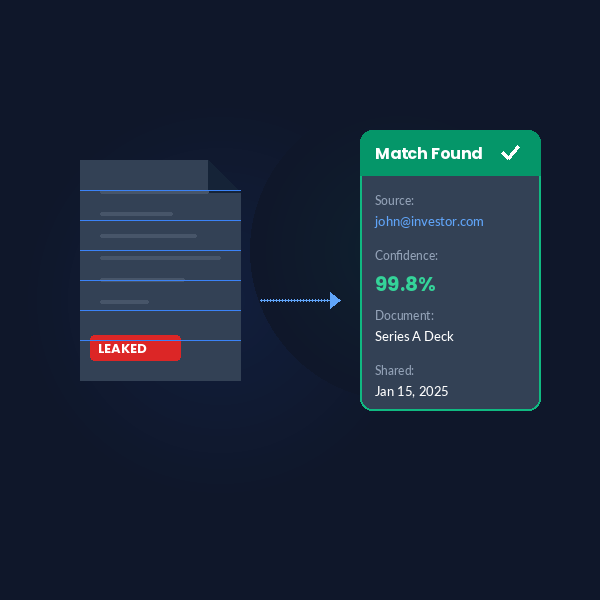
Leak Verification
When you suspect a document has been leaked, simply upload the leaked version. Our system scans for the unique fingerprints within it and tells you exactly which recipient the document came from, enabling you to take swift action.
- Instant leak source identification
- Supports multiple file formats
- Detailed leak analysis reports
- Time-stamped leak detection logs
- Integration with your security workflows
Document Integrity Check
Upload any incoming document — contracts, financial statements, invoices, certificates — and get an instant integrity score. Veriflo runs forensic analysis on PDF metadata, creation dates, software signatures, and structural patterns to flag documents that may have been manipulated.
- Instant integrity scoring from 0-100
- Risk level classification (clean, low, medium, high, critical)
- PDF metadata and structure analysis
- Creation/modification date gap detection
- Editing software and tool detection
- Suspicious pattern identification
Forensic Tamper Detection
Our forensic engine goes beyond surface-level checks. It detects incremental saves that indicate post-creation editing, identifies mismatches between document creator and producer software, flags JavaScript or embedded files hidden inside PDFs, and spots metadata that has been stripped or altered — all signs of potential document fraud.
- Incremental save detection (multiple %%EOF markers)
- Creator/producer software mismatch analysis
- Hidden JavaScript and embedded file detection
- Image EXIF metadata and compression analysis
- Hash comparison against known originals
- Veriflo fingerprint verification on incoming docs
Real-Time Access Tracking
Get comprehensive visibility into every interaction with your shared documents. Track who opened documents, how long they viewed them, what devices they used, and where they were located when accessing the documents.
- Real-time access notifications
- Geographic tracking by IP address
- Device type and OS information
- Time spent viewing documents
- Customizable alerting thresholds
- Exportable analytics reports
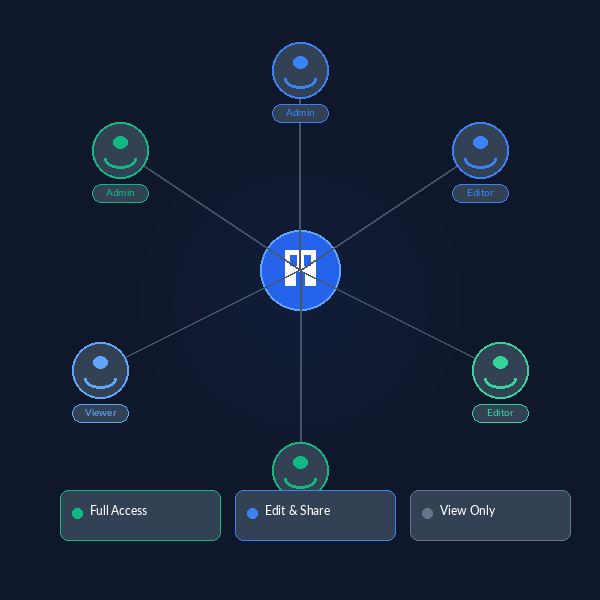
Team Collaboration
Manage document sharing and access across your entire team with granular permission controls. Assign roles, manage team members, and maintain security while enabling seamless collaboration.
- Role-based access controls
- Multiple team management
- Delegated distribution permissions
- Team member activity logs
- Collaborative document sharing
- Audit trails for team actions
Enterprise Security & Compliance
Enterprise-grade security features ensure your sensitive documents are protected with industry-leading standards. Full audit trails, encryption, and compliance certifications give you peace of mind.
- AES-256 encryption in transit and at rest
- SOC 2 Type II compliance ready
- Comprehensive audit logging
- HIPAA and GDPR compliance support
- IP whitelisting and SSO/SAML
- Dedicated security contact
Why Choose Veriflo?
See how we compare to traditional document sharing
| Feature | Veriflo | Cloud Storage | |
|---|---|---|---|
| Invisible Fingerprinting | |||
| Leak Detection | |||
| Document Integrity Check | |||
| Tamper Detection | |||
| Real-Time Tracking | |||
| Access Revocation | |||
| Expiring Links | |||
| Audit Logs | |||
| Team Management | |||
| Enterprise Security |
Ready to protect your documents?
Start your free trial today. No credit card required.