Protect Outgoing. Verify Incoming.
Two workflows, one platform. Fingerprint and track the documents you send out, and verify the documents you receive for signs of tampering.
Protect Outgoing Documents
Fingerprint, share, track, and identify leaks
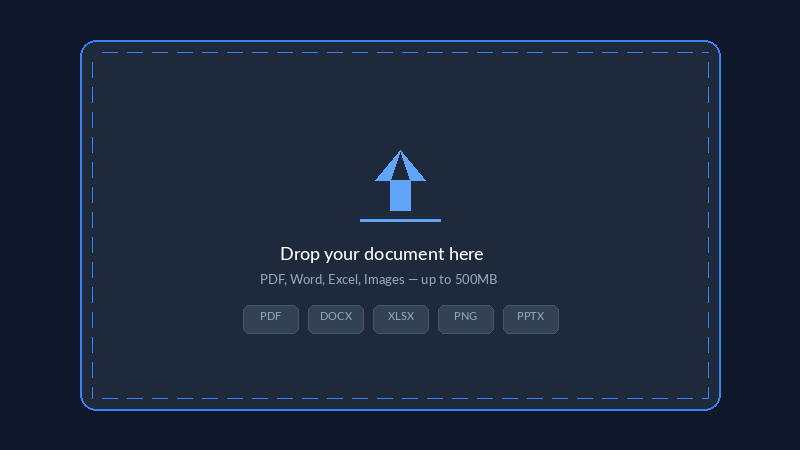
Upload Your Document
Start by uploading your confidential document to Veriflo. We support PDF, Word, Excel, PowerPoint, images, and more.
You can:
- Drag and drop or click to upload
- Support for documents up to 500 MB
- Automatic virus scanning
- Instant encryption at rest
What Happens: Your document is encrypted with AES-256 and stored securely. We prepare it for fingerprinting while keeping your original intact.
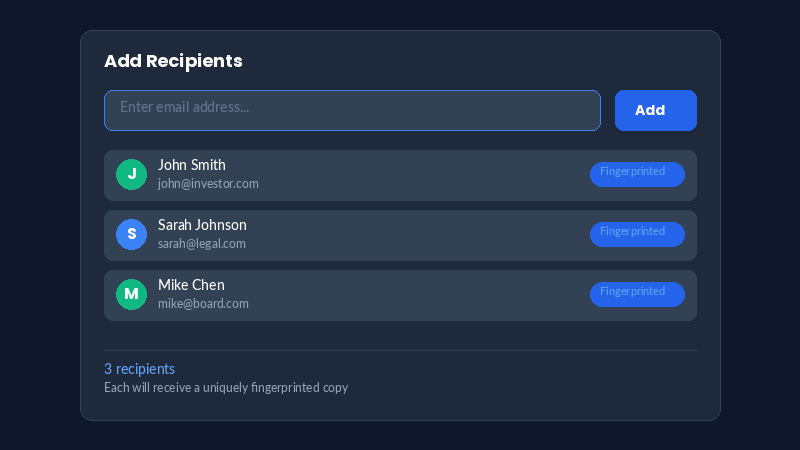
Add Recipients & Enable Fingerprinting
Select who should receive copies of your document and configure sharing preferences.
You can:
- Add individual recipients by email
- Create distribution groups
- Set custom recipient names
- Configure access permissions
What Happens: Veriflo creates a unique fingerprint for each recipient. These invisible markers embed recipient identifiers throughout their copy of the document.
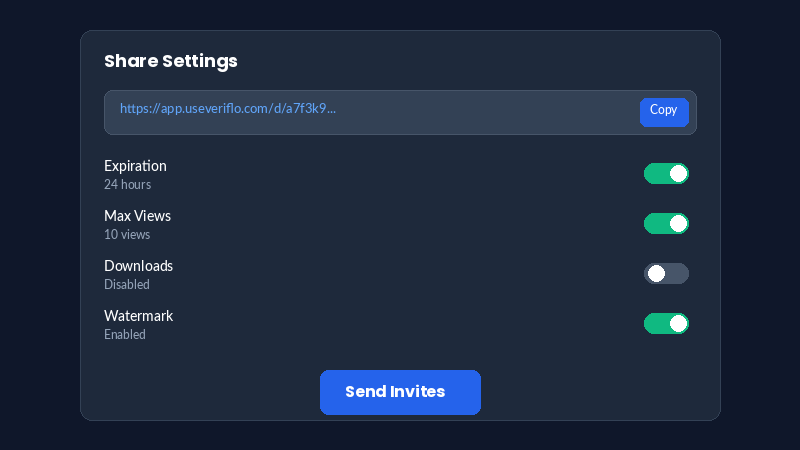
Share with Secure Links
Generate unique, tracked sharing links for each recipient. You control every aspect of access.
You can:
- One unique link per recipient
- Set expiration dates (hours to days)
- Control maximum view counts
- Allow/disallow downloads
What Happens: Recipients receive an email with their secure link. When they click, they get their unique fingerprinted copy. All access is logged in real-time.
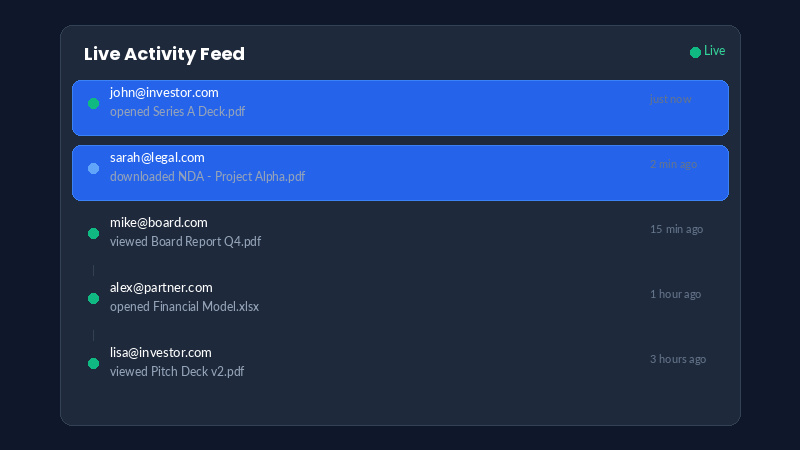
Monitor Access & Activity
Watch in real-time as recipients view your documents. Track exactly who accessed what and when.
You can:
- Real-time access notifications
- View counts and time spent
- Geographic location tracking
- Device and browser information
What Happens: Get instant alerts when documents are accessed. Monitor suspicious activity patterns and unusual viewing behavior across your dashboard.
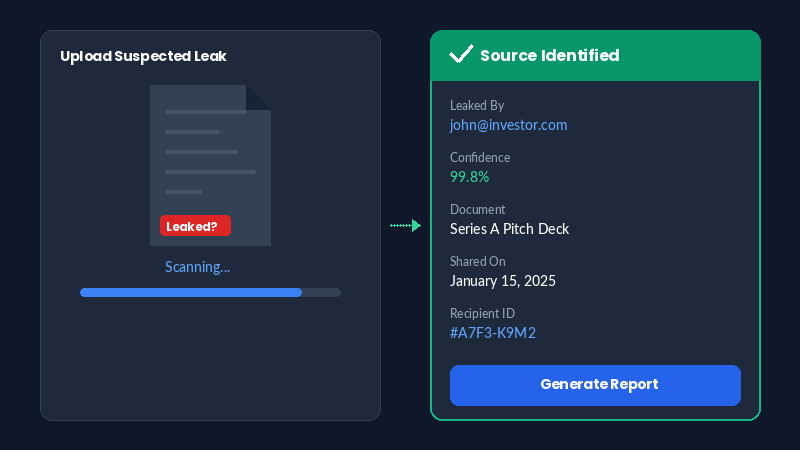
Verify & Identify Leaks
If you suspect a leak, upload the leaked document to instantly identify which recipient it came from.
You can:
- Upload suspected leaked document
- Instant forensic analysis
- Identification of source recipient
- Generate investigation reports
What Happens: Our system scans the leaked document for embedded fingerprints. Within seconds, you know exactly which recipient's copy was leaked.
Verify Incoming Documents
Check for tampering, fraud, and manipulation before you act
Upload a Document to Verify
Drag and drop any incoming document — contracts, financial statements, invoices, certificates — into the Integrity Check tool.
You can:
- Supports PDF, images (JPEG, PNG), and more
- Drag and drop or click to upload
- No account needed for basic checks
- Documents are not stored permanently
What Happens: Veriflo begins forensic analysis immediately. The document is scanned for metadata, structural patterns, and signs of manipulation.
Forensic Analysis Runs Automatically
Our engine performs multiple forensic checks on the document in seconds, examining metadata, structure, and content for signs of tampering.
You can:
- PDF metadata and creation date analysis
- Creator/producer software mismatch detection
- Incremental save and structural anomalies
- Image EXIF data and compression analysis
- Hidden JavaScript and embedded file detection
- Hash comparison against known originals
What Happens: Each check produces findings that are classified as informational, warning, or danger. These feed into an overall integrity score.
Get Your Integrity Score
Receive an instant integrity score from 0 to 100, with a clear risk level and detailed findings explaining exactly what was detected.
You can:
- Score from 0-100 with visual gauge
- Risk levels: Clean, Low, Medium, High, Critical
- Expandable findings with severity ratings
- Technical details for deeper investigation
- Veriflo fingerprint detection (if present)
- Exportable results for your records
What Happens: You get a clear, actionable assessment of whether the document appears genuine or shows signs of manipulation — so you can make informed decisions before acting on it.
Key Principles
Veriflo is built on these core principles to keep your documents safe
End-to-End Security
Every document is encrypted with AES-256. Only you and intended recipients can access content.
Zero-Trust Tracking
Never trust an unsecured document. Every copy is uniquely marked so leaks are instantly traceable.
Verify Before You Trust
Don't assume incoming documents are genuine. Run integrity checks to detect tampering before making decisions.
Instant Notifications
Get real-time alerts when documents are accessed, shared, or suspicious patterns detected.
Full Control
You control access. Revoke links, set expirations, and limit downloads with complete flexibility.
Enterprise Grade
SOC 2 certified, HIPAA compliant, and designed for organizations with strict security requirements.
Common Questions
How long do documents stay encrypted?
Can recipients share the document with others?
What happens if I revoke access?
How accurate is leak detection?
How does the integrity check work?
What does the integrity score mean?
Is there a learning curve?
Ready to secure your documents?
Start your free trial. Upload your first document in under 60 seconds.